Identity and Access Management V2
ThoughtSpot supports an industry-standard cloud authentication method through Okta. With this feature, ThoughtSpot powers its internal authentication with Okta, which is the industry-leading authentication platform. The change to Okta is internal and has no impact on customers. After ThoughtSpot enables this feature by default, all user authentication will automatically use the internal Okta service. This feature set involves several external improvements to authentication, including security enhancements.
ThoughtSpot is committed to continuously enhancing your security, administration and operations experience. Beginning with ThoughtSpot version 10.0.0.cl we are upgrading our Identity and Access Management (IAM) capabilities to provide a more secure login and authentication experience.
Migration of all ThoughtSpot customers will be done in phases as part of the upgrade maintenance window. You can also request the upgrade by contacting ThoughtSpot support.
The following are some of the enhancements that come with this upgrade:
-
Advanced password management policies that allow for greater security and flexibility.
-
Enhanced enterprise-grade security compliance, and advanced identity features supported with IAM V2.
-
New features will only be supported with IAM V2.
The chart below outlines the differences between IAM V1 and IAM V2:
Feature |
IAM V1 |
IAM V2 |
Local user management |
Yes |
Yes |
SAML |
Yes |
Yes |
OpenID Connect (OIDC) |
Yes |
Yes |
Active Directory Sync |
Yes |
Yes |
SAML per Org |
No |
Yes |
OIDC per Org |
No |
Yes |
Org and Group mapping per user from identity provider (IDP) |
No |
Yes |
Multifactor authentication (MFA) support for local users (Beta) |
No |
Yes (Beta) |
To set up your ThoughtSpot environment for IAM V2, complete the following procedures.
Before migrating to IAM V2
To set up your ThoughtSpot environment for IAM V2, complete the following procedures.
| In keeping with IAM best practices, and due to user workflows for self-serve password resets, email addresses are mandatory for all users on TS cloud clusters for successful IAMv2 migration. |
Allowlist URLs
Users will be redirected to these URLs when they sign in.
| If these URLs are not allowlisted, users will be unable to access your ThoughtSpot instance after migration to IAM V2. |
-
Update your Network/Firewall approved URL settings allowlist to include the following URLs:
-
For US and Asia-Pacific (APAC): https://identity.thoughtspotlogin.cloud
-
-
To verify accessibility to these URLs, browse to our validation cluster:
validate-iamv2.thoughtspot.cloud.The ThoughtSpot Login page appears.
-
Enter any credentials, which should result in a failure page. If you get this error, then you have access to the necessary URLs.
After migrating to IAM V2
Depending on your configuration, you will need to complete the following after migrating to IAM V2.
Customers with only local accounts
After migration, local user accounts will be successfully migrated.
-
Please notify your ThoughtSpot users that they will be prompted to enter their username and password after migration.
If MFA (Beta) is configured, users will be prompted to complete two-factor authentication. If users forget their username that is required for the Forgot Password workflow they will not be able to reset their password. -
To validate local account migration, create a user in ThoughtSpot and validate that user creation is successful.
Customers with SAML and local accounts
After migration, authentication will continue as normal for customers with IAM configured. Complete the following steps to migrate to IAM V2.
| Until you complete these steps, your SAML configuration is read-only, and you will be unable to edit this configuration. |
-
From the drop-down at the top right side of the navigation bar, select the Admin tab.
-
Select Authentication > SAML from the left side navigation pane.
The following displays:
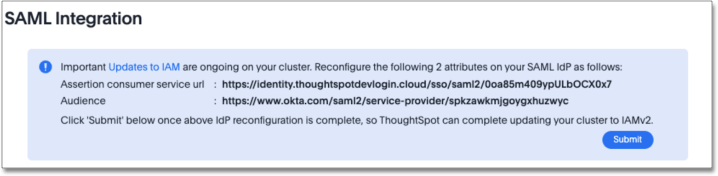
-
Request that your IdP administrator configure the following attributes for ThoughtSpot to the values displayed.
-
Assertion Consumer Service URL (Single Sign On URL on IdP)
-
Audience (EntityId on IdP)
-
-
Click Submit when the configuration on your IdP is complete.
This reloads the service. Your configured SAML URLs will now appear on the page.
-
Optionally, you can add a cluster URL in your SAML application as default relay URL.
With IAMv2, the SAML response must have an email attribute. Ensure the email is being sent via SAML response and the email attribute are mapped correctly in Edit SAML connection > Map attributes.
Validate your SAML account migration
-
Validate that the SAML attributes mapped in ThoughtSpot after migration are identical to pre-migration attributes.
-
Sign in to ThoughtSpot as a SAML user and verify that your authentication is successful.
You can now map certain Identity Provider (IDP) attributes from the ThoughtSpot Admin Console when configuring OIDC or SAML authentication. These attributes include the username, email, and display name. For more information, see Managing authentication with SAML using IAMv2 and Managing authentication with OIDC using IAMv2. After you configure OIDC or SAML authentication, only Okta interacts with your IDP. Your ThoughtSpot cluster does not directly interact with your IDP.
The users section of the Admin Console now supports account activation monitoring. If a user still needs to activate their account, administrators can see that information in the Users section and re-send their activation email. For more information, see Create, edit, or delete a user using IAMv2.
Local users now create their own password during activation. Administrators do not create the password prior to activation. For more information, see Activate your ThoughtSpot account using IAMv2.
Note that whenever you navigate to the login page for ThoughtSpot, you will temporarily see the following URL: identity.thoughtspot.com. This is an expected part of the IAM V2 login experience.
Refer to the following articles for detailed information on new or changed ThoughtSpot functionality with IAMv2:
-
Managing authentication with SAML using IAMv2: If the SAML section of the Admin Console is called SAML integration, your company is using IAMv2.
-
Managing authentication with OIDC using IAMv2: If the OIDC section of the Admin Console is called OIDC integration, your company is using IAMv2.
-
Create, edit, or delete a user using IAMv2: If the Users section of the Admin Console contains an Account Activation column, your company is using IAMv2.
-
Account activation using IAMv2: If your activation email subject line is "Activate your ThoughtSpot account," your company is using IAMv2.
Refer to the following articles for detailed information on ThoughtSpot functionality if you do NOT have IAM V2 enabled. Note that there is no account activation required for local users on clusters that do not have IAM V2 enabled.
-
Managing authentication with SAML: If the SAML section of the Admin Console is called Authentication: SAML, your company is not using IAM V2.
-
Create, edit, or delete a user in a single-tenant environment: If the Users section of the Admin Console does not contain an Account Activation column, your company is not using IAM V2.
| After migrating to IAM V2, usage of space and special characters will not be allowed while creating Orgs. This is to keep Org names DNS compliant. This restriction applies to only new Org names and does not impact existing Orgs. |



