Configure SSL
Secure socket layers (SSL) provide authentication and data security when sending data to and from ThoughtSpot.
You can use your own SSL certificate to secure ThoughtSpot HTTP(S) traffic.
ThoughtSpot Training
For best results, we recommend that you take the following ThoughtSpot U course: Nginx SSL.
See other training resources at ThoughtSpot U.
About SSL
To enable SSL for the ThoughtSpot web service, you must provide your organization’s SSL certificate for the ThoughtSpot service URL. If you do not have this certificate, you have the following options:
-
Check with your IT department to see if they have an SSL certificate you can use.
-
Obtain the certificate from an issuing authority.
-
Use the default SSL certificate on the ThoughtSpot nodes.
-
Disable SSL using the
tscli ssl offcommand.
ThoughtSpot supports a wide variety of SSL types.
Required ports
To use ThoughtSpot webservice securely, ensure that TCP port 443 is open to accommodate incoming connections to ThoughtSpot nodes and clusters.
Configure SSL for web traffic
To add SSL and enable HTTPS in ThoughtSpot, generate the Certificate Signing Request (CSR) and obtain the SSL certificate chain and the private key.
You can then configure SSL using tscli or through the Admin Console, and then test the SSL certificate.
Certificate Signing Request
When you generate a CSR, you handle sensitive data. Therefore, ThoughtSpot recommends that its customers generate their own CSRs.
You can generate a CSR in several ways. Most often, you generate a CSR and a new private key at the same time. If you already have a private key, use it to generate a CSR.
Follow these steps to generate a CSR and a private key. You need a computer you can run Linux commands on, and a recent version of openssl.
-
sshinto one of your ThoughtSpot nodes.ssh admin@<node_IP> -
Run the command to generate a CSR and private key pair:
openssl req -new -newkey rsa:2048 -nodes -out csr.pem -keyout pk.key[-subj "/key1=value1/key2=value with space/Note the following parameters:
- key bits
-
ThoughtSpot supports both 2048 and 4096-bit keys.
- subj
-
A common subject. Logically equivalent to the
-dnameproperty of keytool. Alternatively, you can skip this flag, andopensslprompts you to enter this information interactively. - add-multivalue-rdn
-
Optionally, run
add-multivalue-rdnto allow multiple values to be set for the same key. - man req
-
Run
man reqfor more details.
If you already have a private key, you can use it to generate a CSR. Follow these steps to generate a CSR with an existing private key:
-
sshinto one of your ThoughtSpot nodes.ssh admin@<node_IP> -
Run the command to generate a CSR and private key pair:
openssl req -new -key <private_key_file> -nodes -out csr.pem[-subj "/key1=value1/key2=value with space/Specify the existing private key file.
SSL certificate chain
The SSL certificate chain must be in PEM format, which is an X.509v3 file that contains ASCII (Base64) armored data, packed between BEGIN and END directives.
The certificate chain may contain a series of certificates, with the root certificate at the bottom and user-facing, while the ThoughtSpot-specific SSL certificate is at the top.
Private key
The private key must also be in compatible PEM format. It cannot be password-protected, or passphrase-protected.
| Do not use a passphrase when creating certificates with ThoughtSpot. |
If you are prompted to specify a passphrase, first check if it exists by invoking the following command:
openssl rsa -check -in pk.key`If the answer is 'yes', you must remove the passphrase first, and then proceed to use the private key with ThoughtSpot.
Configure SSL using tscli
Follow these instructions to install the SSL certificate using tscli:
-
Use the instructions from the certifying authority where you obtained the certificate.
This is usually sent to you by email, or available for download.
-
Copy the certificate and key files to ThoughtSpot:
$ scp <key> <certificate> admin@<IP_address>:<certificate-path> -
Log in to the Linux shell using SSH.
-
Change to the directory where you copied the files:
$ cd <certificate-path> -
To install the certificate, issue the
tsclicommand:$ tscli ssl add-cert <key> <certificate> <IP_address_or_URL> -
To test that the certificate is correctly installed, sign in to the admin account.
You should see that the application’s URL begins with
https://.
Set the recommended TLS version
ThoughtSpot supports SSL v3, TLS v1.2 by default. Support for TLS v1.0 and v1.1 is included for backwards compatibility. To ensure support for TLS version 1.2:
-
Enable your web browser to support TLS v1.2. This can be done in your browser’s advanced settings.
-
Log in to the Linux shell using SSH and run command:
tscli ssl tls-statusIt should respond with
Minimum TLS version supported: 1.2This will block all usage of older versions.
-
To change this, run
tls ssl set-min-tls-version 1.1ortls ssl set-min-tls-version 1.0as desired for backward compatibility.
Configuration string for load balancers
When enabling SSL support on a load balancer’s server-side SSL client profile, add support for the following ciphers to ensure compatibility between the load balancer and ThoughtSpot:
| TLSv1.2:
| ciphers:
| TLS_DHE_RSA_WITH_AES_128_GCM_SHA256 - strong
| TLS_DHE_RSA_WITH_AES_256_CBC_SHA - strong
| TLS_DHE_RSA_WITH_AES_256_CBC_SHA256 - strong
| TLS_DHE_RSA_WITH_AES_256_GCM_SHA384 - strong
| TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 - strong
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA - strong
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 - strong
| TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 - strong
| compressors:
| NULL
|_ least strength: strongTo construct the cipher string, note this pattern:
EECDH+AESGCM:EDH+AESGCM:AES256+EECDH:AES256+EDHYou can retrieve these from the ThoughtSpot web server (not against the load balancer) by running the following command on any ThoughtSpot node:
nmap --script ssl-enum-ciphers -p 443 <ThoughtSpot_node_IP_address>You must ensure that your load balancer supports these ciphers. If your load balancer cannot support these ciphers, contact ThoughtSpot support.
Configure SSL through the Admin Console
To configure SSL, follow these steps:
-
Navigate to the Admin Console by clicking on the Admin tab from the top navigation bar.
-
Select Security from the side navigation bar that appears.
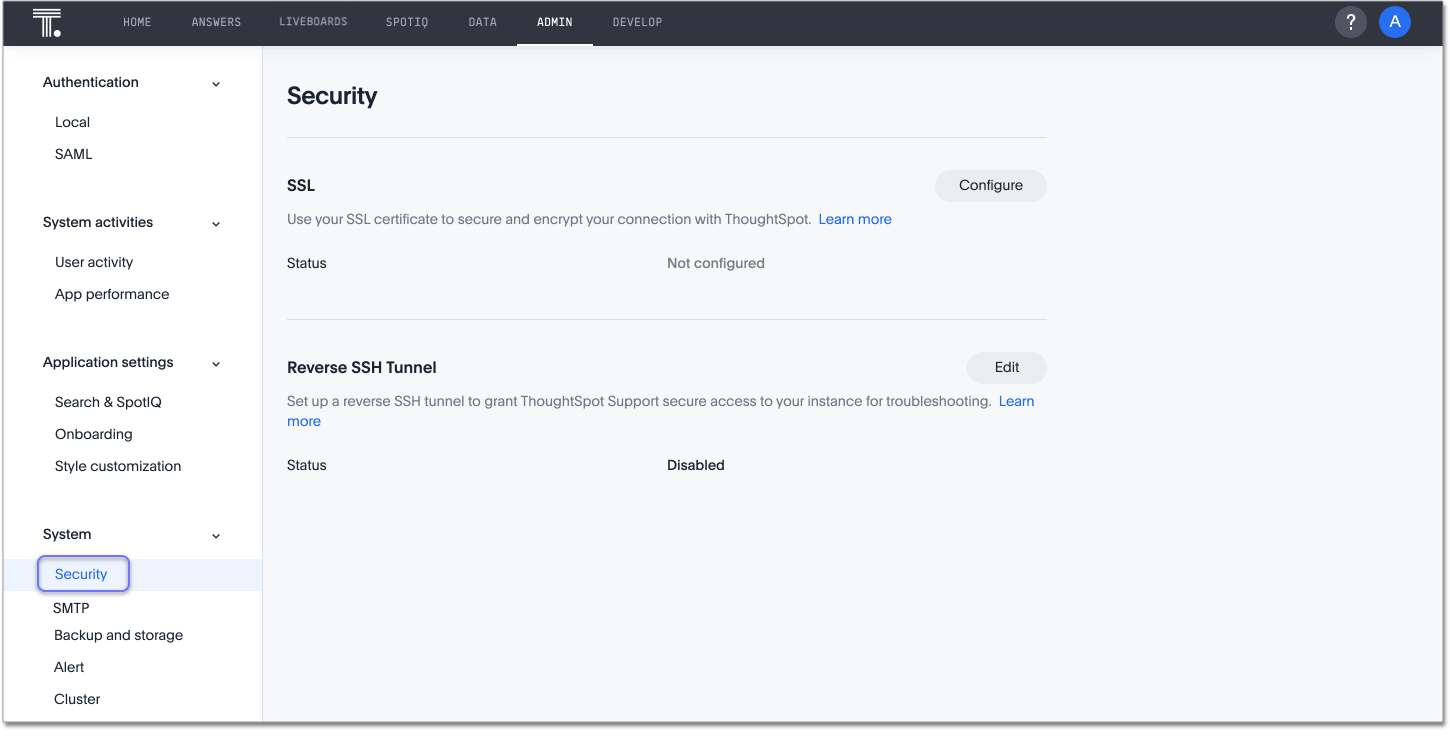
-
Click Configure.
-
Fill out the following parameters:
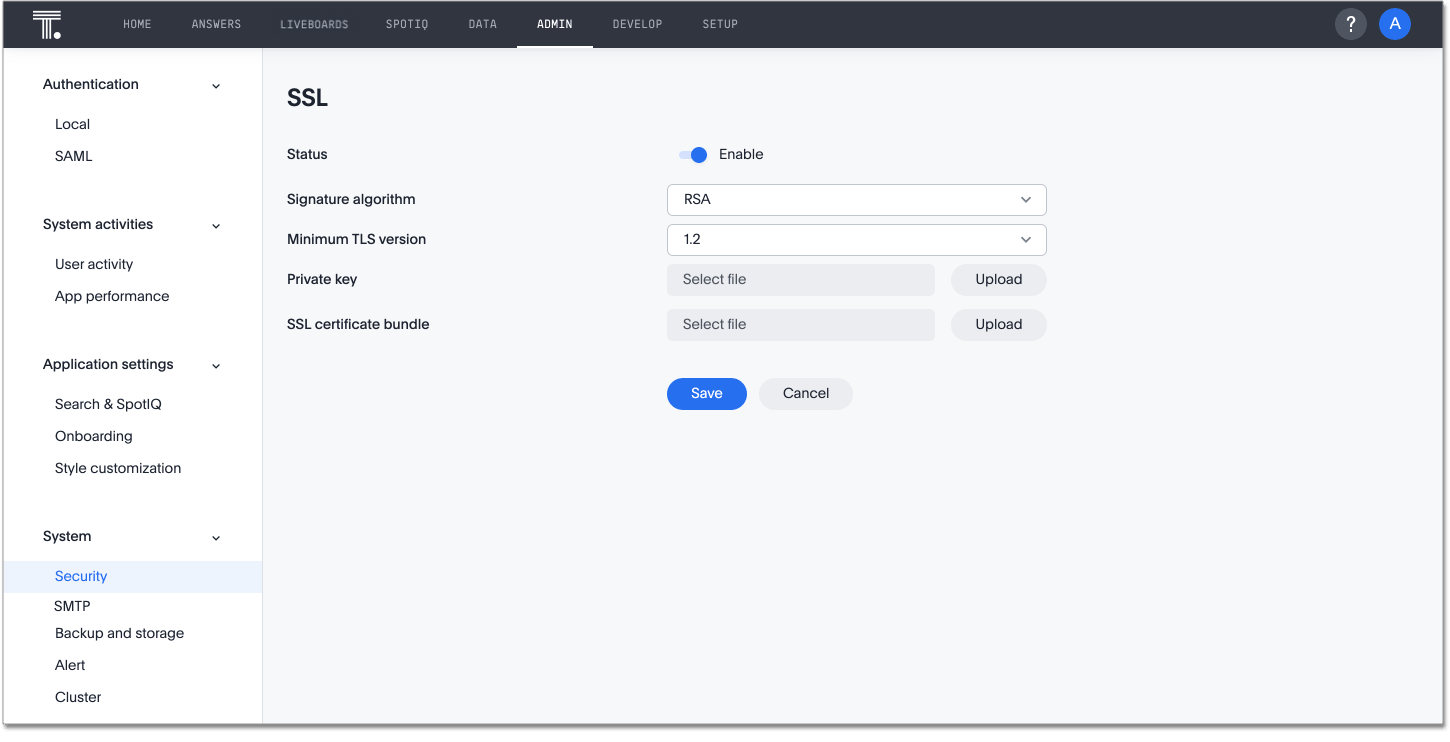
- Status
-
Toggle the switch to Enable.
- Signature algorithm
-
Choose RSA.
- Minimum TLS version
-
Choose TLS 1.2 as a best practice.
ThoughtSpot also supports TLS 1.1 and 1.0; set the minimum supported version to 1.1 or 1.0 to use these versions.
- Private key
-
Attach your private key file.
- SSL certificate bundle
-
Attach your SSL certificate bundle file.
-
Click Save.
Test the SSL certificate
To test if the certificate is installed correctly, see Sign in to the ThoughtSpot application.



