Configure OAuth for a Databricks connection
ThoughtSpot supports OAuth for a Databricks connection. This page describes the setup and configuration required.
Databricks SQL warehouses are configured with OAuth 2.0 authentication. ThoughtSpot supports all IDPs supported by Databricks in OAuth 2.0, including Microsoft Azure’s Azure Active Directory (AAD), AWS, and Okta. As an example, this article documents how to set up OAuth for Microsoft Azure AAD.
| For OAuth, we recommend checking the Databricks documentation to confirm any IDP support and their details. This article documents only the most frequently set-up IDP. |
Part 1: Create an application in AAD
To create an application in AAD, do the following:
-
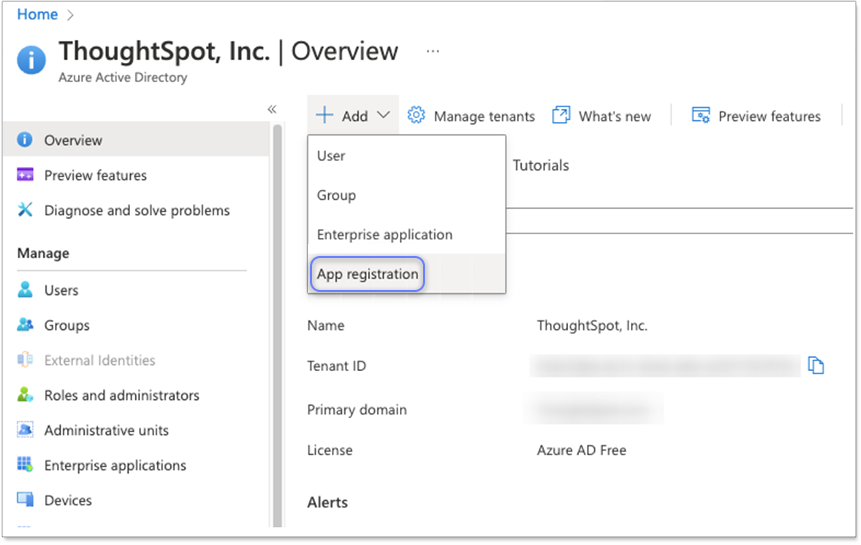
Log in to the Azure portal and navigate to the AAD resource, click Add, and select App registration.
-
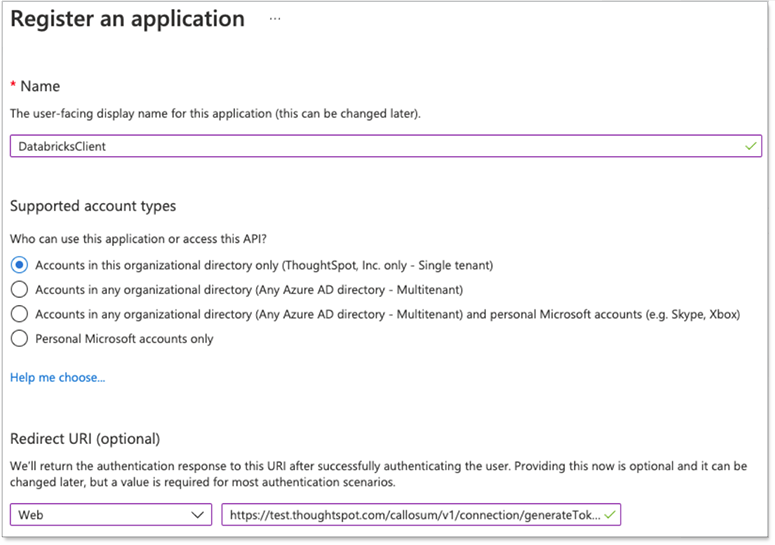
Provide a name for your application and add a redirect URI in the following format:
https://<your-thoughtspot-instance>/callosum/v1/connection/generateTokensThis is where the call is redirected upon successful login to AAD when creating a connection in ThoughtSpot.
-
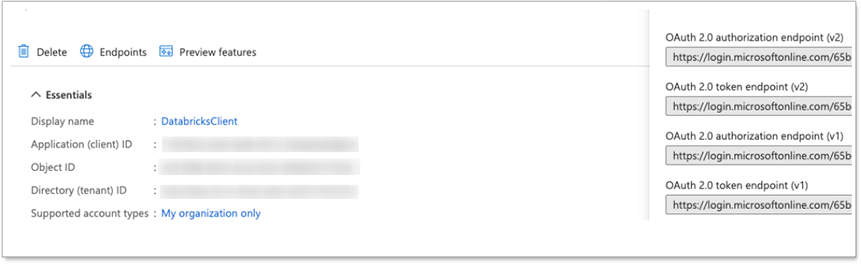
After you register your application, make a note of the Application (client) ID in the Essentials section of the app’s overview page. Also, make a note of the OAuth 2.0 authorization and token endpoints. These are required later when configuring the Databricks connection in ThoughtSpot.
Part 2: Configure the AAD application
To configure the AAD application, do the following:
-
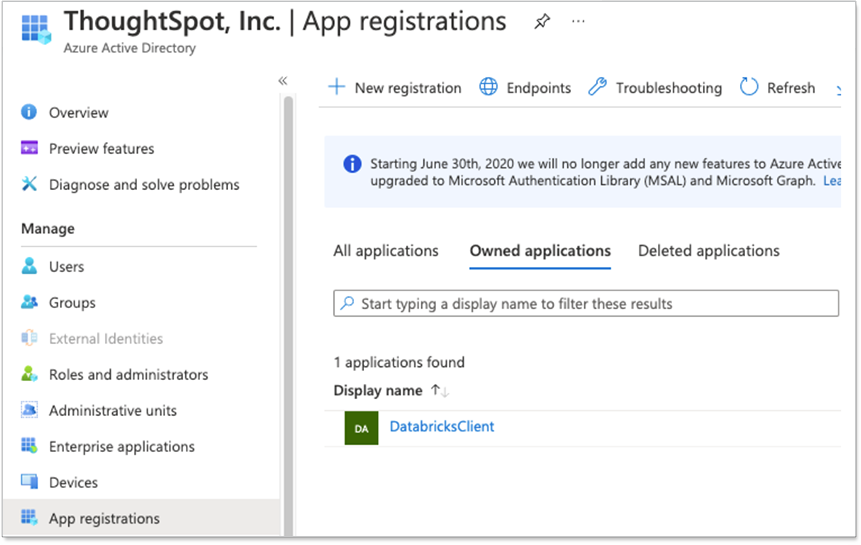
In the Azure portal, navigate to your application by selecting App Registrations and then clicking your newly registered application to open it.
-
In your application, select API Permissions and under the AzureDatabricks API/Permissions name, click the user_impersonation permission.

-
Select Certificates & secrets and create a new secret for the app, providing an appropriate expiry time. Make a note of the secret value because it is displayed only while creating it. The secret value is required later when you create the Databricks connection in ThoughtSpot.
Part 3: Create AAD users in the Databricks workspace
To create AAD users in the Databricks workspace, do the following:
-
Log in to the Databricks workspace as a user with admin privileges. Select Setting and navigate to Admin Console.
-
Select Add User to create AAD users in Databricks.
Part 4: Connect the client using the OAuth token
The JDBC connection URL which uses the access token from AAD must use the following format:
`"jdbc:spark://adb-111222444555.13.azuredatabricks.net:443/samples;transportMode=http;" +
"ssl=1;httpPath=/sql/1.0/endpoints/c53335555f2222e999;" +
"AuthMech=11;Auth_Flow=0;" +"Auth_AccessToken=<access_token>"`Related information



