Manage users and groups with SCIM
System cross domain Identity Management (SCIM) allows you to synchronise user management between your IdP and ThoughtSpot. SCIM automates identity management and user provisioning across different identity management systems so that you no longer need to manage users, groups and privileges in multiple platforms. If you use an IdP like Okta, Azure, or Active Directory, with SCIM you can provision users to groups and Orgs and ensure they remain in sync with changes made in the IdP. SCIM provisioning is also per Org, so that you can ensure that users are provisioned to a particular group in a particular Org.
ThoughtSpot supports the following in beta:
-
Automatic provisioning of users with their corresponding groups and Orgs when the users authenticate via SSO (SAML).
-
Automatic updates of user attributes in ThoughtSpot when they are updated in the IdP.
-
When you delete a user from IdP, they are automatically deleted from ThoughtSpot.
Configure SCIM
To configure SCIM on your cluster and automate updates between your IdP and ThoughtSpot, complete the following:
-
Provision capabilities in ThoughtSpot
-
Connect your IdP
Provisioning capabilities in ThoughtSpot
-
Sign in to ThoughtSpot and navigate to the Admin portal.
-
Select All Orgs.
-
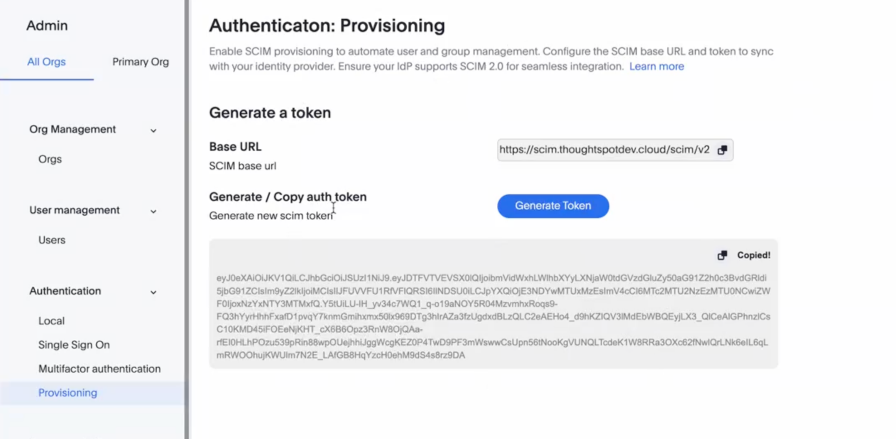
Under Authentication select Provisioning.
Before you configure, ensure that your IdP supports SCIM 2.0 for a seamless integration with ThoughtSpot. -
Enter the SCIM Base URL. This URL identifies the SCIM API endpoint your Identity provider communicates with for every user management and user provisioning change.
-
Click Generate Token to generate and copy the authentication toke. This token is used to authenticate the SCIM service (ThoughtSpot application) in your IdP.
Connecting to Okta
-
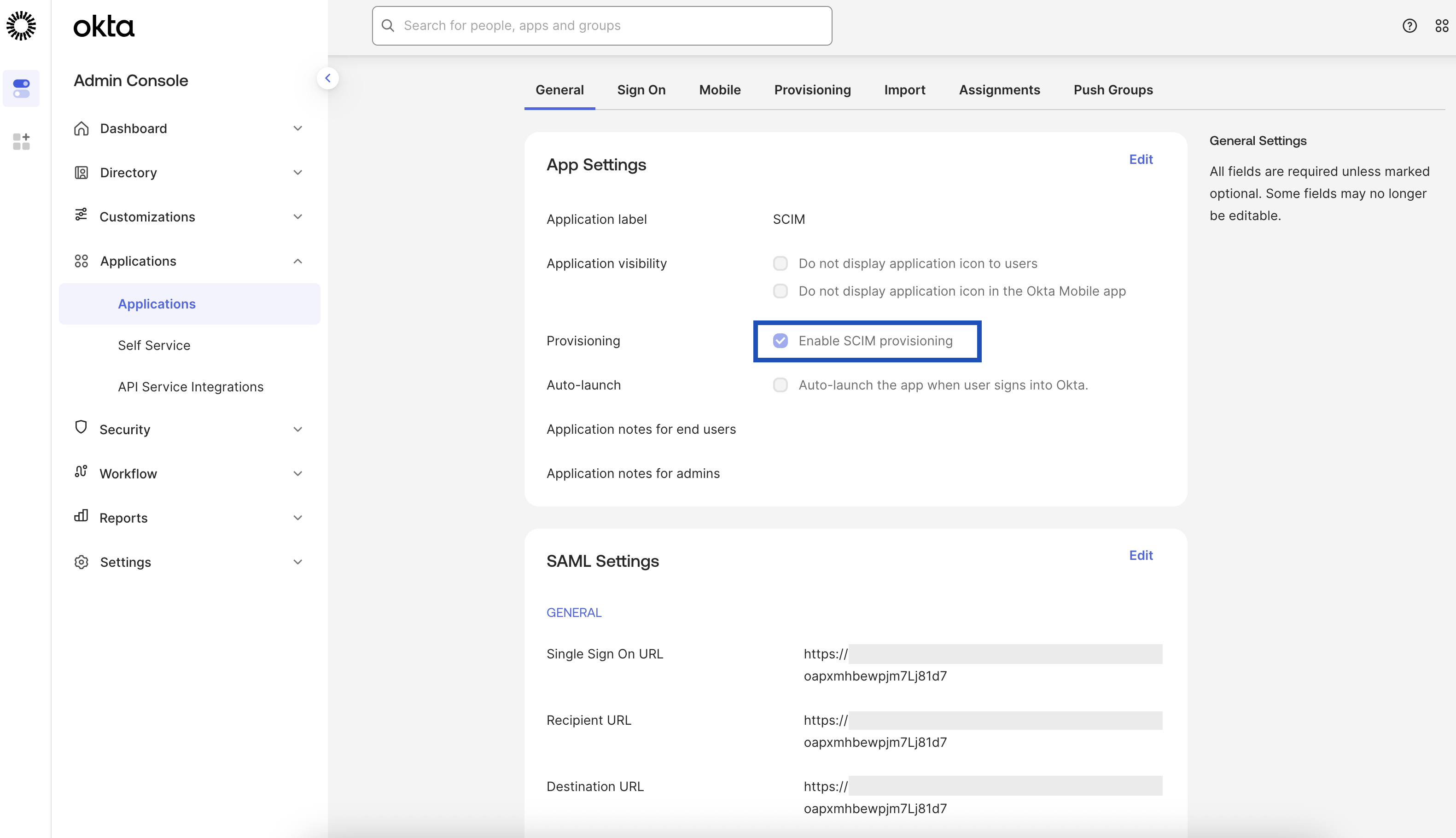
Check if SCIM provisioning is enabled in Okta.
-
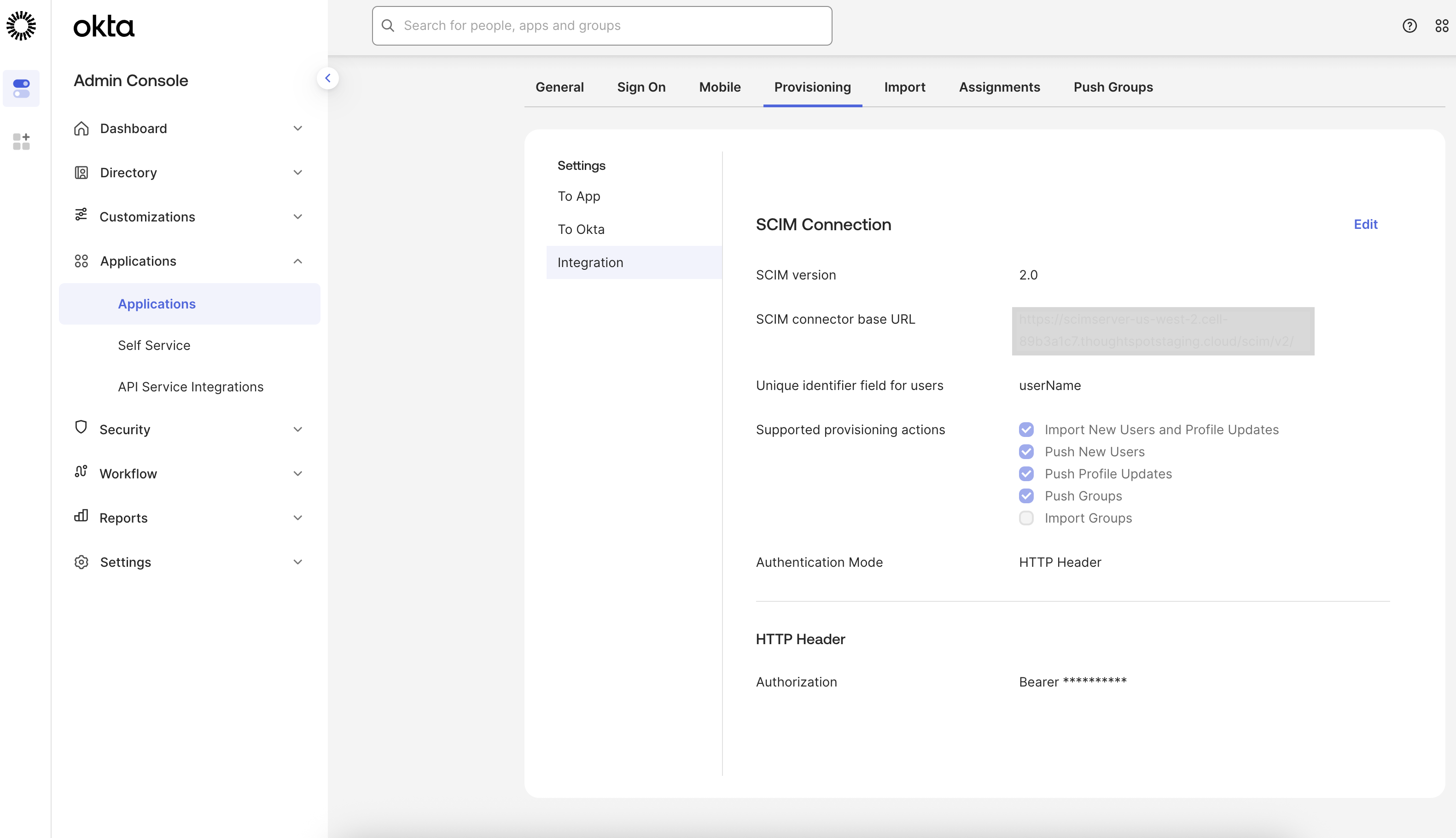
Use the token you generated and copied in ThoughtSpot to set up the authentication between your Okta and ThoughtSpot. Copy the token from ThoughtSpot in the bearer token field provided in the Okta interface.
-
You can then select which user management actions are synced with ThoughtSpot.
ThoughtSpot supports create, read, update, and delete of users and groups, and provisioning users to groups within Orgs. -
You will have to enable the syncing of the create, read, update, and delete of users and groups, between ThoughtSpot and your IdP.
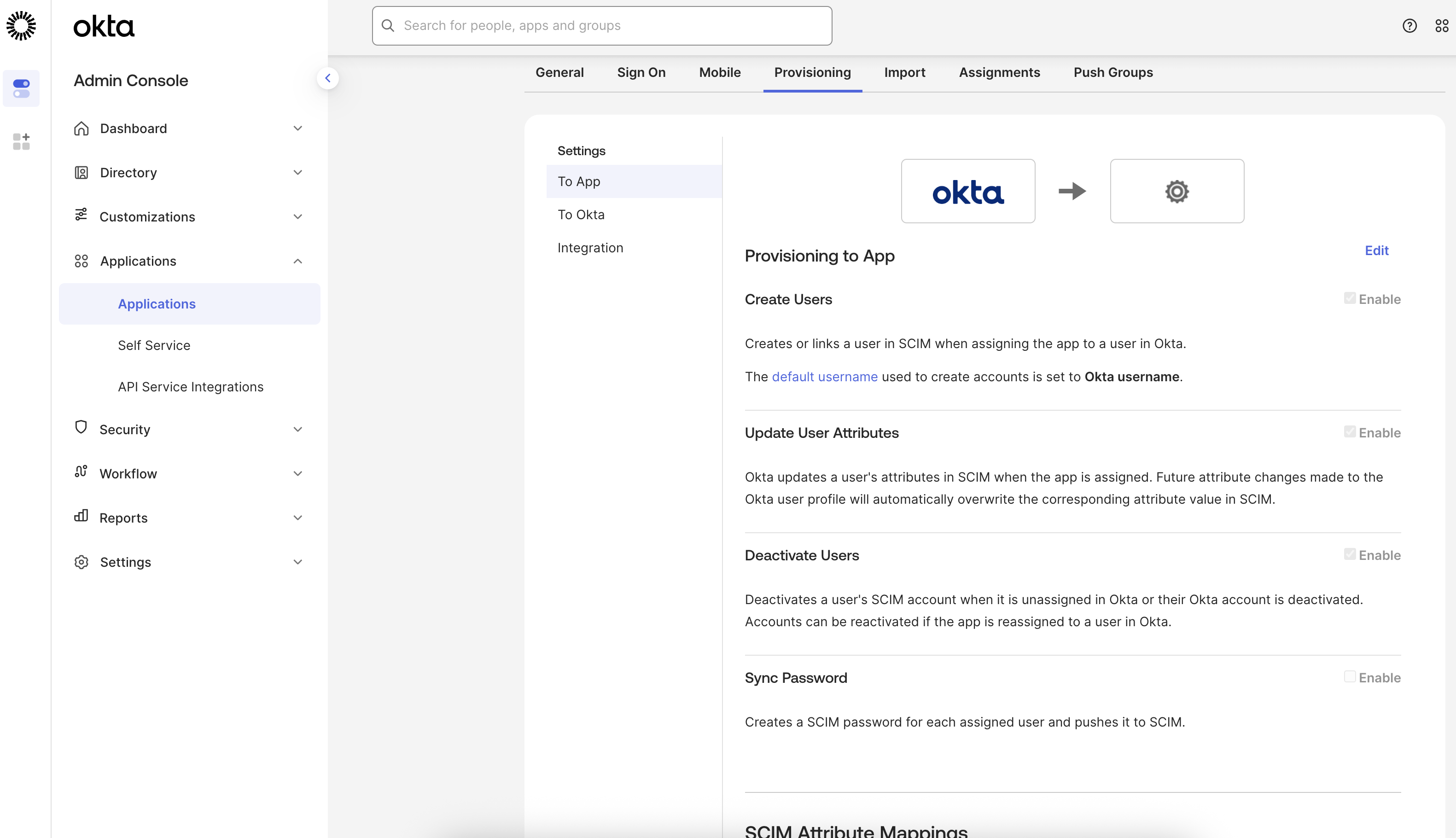
You can add users or create user groups in Okta, assign them to an application and the same will reflect in your ThoughtSpot instance, without having to explicitly sign in to ThoughtSpot.
For more information, see:
Connecting to Microsoft Entra (Azure Active Directory)
For detailed information on enabling SCIM provisioning in Microsoft Entra, see SCIM provisioning in Microsoft Entra.
Testing your configuration
-
Once the configuration and authentication are complete, you can test the configuration by assigning a new user to your ThoughtSpot application in the IdP.
-
Navigate to ThoughtSpot cluster and refresh the page.
-
You should see the newly created user in the user management page in your cluster.
Any of the configured changes done on IdP are reflected on your thoughtSpot cluster.
| Low volume changes made in IdP may be reflected immediately in ThoughtSpot. Larger volume changes are usually reflected within 20 to 40 minutes. |
Best Practices
-
Manage user and group provisioning exclusively from the Identity Provider (IdP). ThoughtSpot should not be used as the source of truth for SCIM managed/ IdP managed users and groups.
-
Regularly rotate SCIM tokens to maintain security and reduce risk from compromised credentials.
-
Monitor audit logs and set up alerting for critical events such as high failure rates, authentication issues, and provisioning delays within your ThoughtSpot instance.
-
Document and follow a structured incident response plan for SCIM-related issues.
-
Use group based access control to simplify user management—add or remove users from groups in the IdP to control their access in ThoughtSpot.
-
Avoid enabling both SAML group mapping and SCIM provisioning simultaneously, as SAML group mapping will override SCIM group assignments on user login.
-
com.thoughtspot.callosum.common.config.OIDCConfiguration#oidcOrgDelimitermust be reviewed to ensure compatibility with groups provisioned via SCIM. If a group name contains this delimiter, the name may be truncated. You can either remove this flag or replace it with an alternative value. Note that each SCIM token has a validity of only six months.
FAQs
-
What are common issues and troubleshooting steps while using SCIM in ThoughtSpot?
-
User not created:
-
Check if the SCIM token is valid and active.
-
Review API logs for errors related to user creation.
-
Verify IdP settings, ensuring the user is assigned to the correct application and SCIM is enabled for the app.
-
Confirm that the user exists and is active in the IdP and that the correct attributes are being sent
-
-
Group not syncing:
-
Validate group mapping in both ThoughtSpot and the IdP.
-
Ensure the group exists in ThoughtSpot if required, or that group creation via SCIM is enabled.
-
Check user assignments to the group in the IdP.
-
Review API logs for group sync errors.
-
-
High provisioning latency:
-
Check ThoughtSpot database performance and health.
-
Review API logs for delays or timeouts in SCIM processing.
-
Monitor for bulk operations or high-volume syncs that may impact performance.
-
-
Unauthorized API requests:
-
Regenerate the SCIM token in ThoughtSpot and update the token in the IdP configuration.
-
Ensure the token has not expired or been revoked.
-
Review API logs for 401/403 errors and confirm the IdP is using the correct endpoint and credentials
-
-
-
How does group and role assignment work with SCIM?
Groups and roles can be managed via SCIM. Membership in a group in the IdP can automatically assign the corresponding role in ThoughtSpot, controlling access levels. When a user is added to a group in the IdP, SCIM syncs this membership to ThoughtSpot, and the user inherits the role privileges assigned to that group.
-
Is SCIM provisioning unidirectional or bidirectional?
SCIM provisioning in ThoughtSpot is unidirectional; changes in the IdP are pushed to ThoughtSpot, but not vice versa. This is a standard for SCIM integrations.
-
What monitoring and alerting are available with SCIM?
Key metrics, including API request success and failure rates, latency, and authentication failures, are closely monitored. Alerts are configured for high failure rates and provisioning issues. This ensures that issues like high error rates, increased latency, or authentication problems are detected and addressed promptly to maintain reliability and performance.
-
Can SCIM be used with SAML or other SSO solutions?
SCIM can be used alongside SAML. SAML group mapping is also supported, which may be simpler if SAML is already configured.



